In light of recent research into the security of end-to-end encrypted cloud storage systems, it’s becoming increasingly clear that while many services claim to offer privacy, few can truly deliver on that promise. A recent paper, End-to-End Encrypted Cloud Storage in the Wild: A Broken Ecosystem (source), analyzed five major E2EE cloud storage providers and found numerous vulnerabilities.
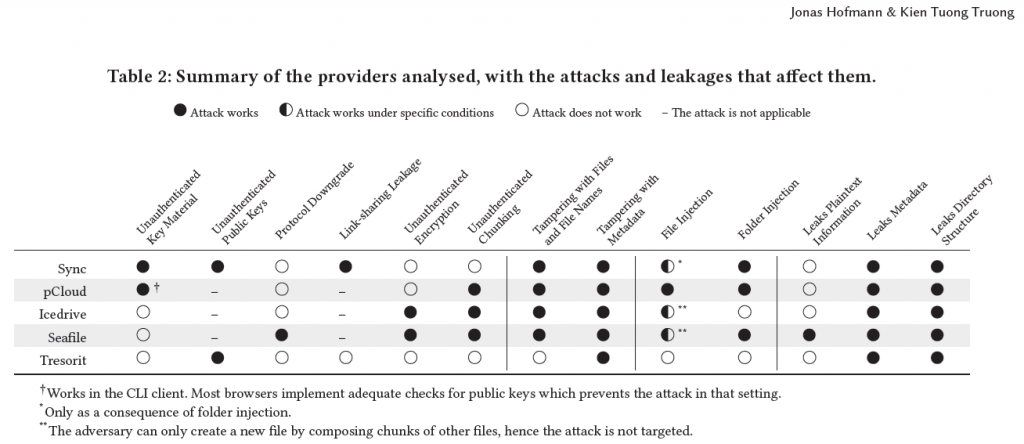
These findings underscore the critical flaws in the cryptographic implementations used by many cloud providers. However, one platform stands apart from these—Züs’s Vult and Blimp. While Züs was not part of the study, we are confident that its unique approach to encryption makes it a far more secure option. As Yury Dabasov, Zus blockchain expert, explains:
“Recent research cited in this article highlights significant vulnerabilities in end-to-end encrypted (E2EE) storage solutions, primarily due to server-generated keys that lack user identities. Zus addresses this issue by anchoring user identities on the blockchain, with all encryption keys (session or re-encryption) derived from this identity. This approach makes Zus an ideal storage solution for safeguarding data and maintaining privacy.”
Security is built into the core of our architecture, ensuring that your data remains fully under your control—no matter what. We are proud to say that the weaknesses identified in the research simply do not apply to us. Here’s why:
1. Unauthenticated Key Material
The paper highlights how providers like Sync and pCloud fail to authenticate key material, allowing attackers to inject malicious keys into the encryption process.
This puts user data at risk. At Züs, however, the encryption keys are securely generated by the client, meaning that blobbers (storage providers) have no access to them and cannot tamper with the data. Our re-encryption feature—powered by master wallet keys—ensures that key material is as secure as a BLS key pair, making any attempt to compromise encryption virtually impossible.
2. Unauthenticated Public Keys
Sync and Tresorit are criticized for using unauthenticated public keys, which can be exploited by a malicious server. Züs solves this problem by ensuring that all public keys are authenticated and derived directly from master wallet keys, preventing unauthorized access and ensuring data confidentiality.
3. Protocol Downgrade
In the case of Seafile, attackers can force a protocol downgrade, allowing them to brute-force user passwords. This attack is not applicable to Züs, as our security protocols remain steadfast against such attempts.
4. Link-Sharing Pitfalls
Sync’s approach to file sharing involves embedding passwords in links, which exposes them to malicious actors. In contrast, Züs ensures that file encryption is personalized—only the intended recipient of a shared file can decrypt it, making this attack vector non-existent.
5. Unauthenticated Encryption Modes
The paper points out that Icedrive and Seafile use unauthenticated cipher modes like CBC, which can be exploited to tamper with file contents. This is not applicable to Züs, as we employ authenticated encryption methods to ensure file integrity.
6. Unauthenticated Chunking
Seafile and pCloud are vulnerable to attacks that involve unauthenticated chunking, allowing files to be tampered with by swapping or removing chunks. At Züs, file integrity is protected by ranged Merkle trees, with the user’s signature on the root. This means it is impossible for any chunk to be tampered with or replaced.
7. Tampering with File Names and Locations
Other providers fail to cryptographically bind file names and locations to their contents, making it possible for attackers to swap or move files around. In Züs, every upload request is signed by the user, ensuring that file names and locations cannot be tampered with.
8. Tampering with File Metadata
The lack of metadata authentication in other systems is another vulnerability highlighted in the paper. Züs takes metadata security seriously: all metadata is authenticated, making it impossible for attackers to alter file sizes, types, or modification dates without detection.
9. Injection of Folders and FilesEncryption Key Management Vulnerabilities
Sync and pCloud are vulnerable to attacks that allow a malicious server to inject folders or files into a user’s storage. Züs has implemented robust protections that prevent any unauthorized file or folder injections, ensuring that only the user can control their storage.
10. Encryption Key Management Vulnerabilities
A major vulnerability in Mega‘s encryption scheme lies in handling encryption keys. Mega generates RSA-encrypted keys, but these keys are shared with the server as ciphertext. This ciphertext is stored on the server, and with certain complex mechanisms, it can be exposed if an adversary gains access to the server (e.g., through a man-in-the-middle attack). This introduces a significant risk to data confidentiality.
In contrast, Züs employs a more secure approach. Encryption keys, including session keys and re-encryption keys, are generated on the fly, within the user’s control, and are never stored on the server. Only the re-encryption key is shared, and this is securely transmitted to the designated blobber or 0box. This method ensures that no keys are stored on the server, providing robust protection even in the event of a server breach.
A Call to the Authors: Test Vult and Blimp for True Security
If the findings in the ETH paper are correct, then re-encryption is a game-changing feature for cloud storage security. No one else offers this level of protection, and we believe it’s crucial for researchers, developers, and security professionals to consider Züs as the gold standard in secure cloud storage.
To further understand the cutting-edge cryptographic approaches Züs utilizes, we invite you to explore the following papers, which demonstrate the power of proxy re-encryption and key splitting—core principles integral to Züs’s platform:
Sharing of Encrypted Files in Blockchain Made Simpler
By: S. Sharmila Deva Selvi, Arinjita Paul, Siva Dirisala, Saswata Basu, C. Pandu Rangan
This paper introduces Proxy Self Re-encryption (SE-PRE), a highly efficient cryptographic technique designed for secure file sharing in blockchain-enabled distributed cloud storage. SE-PRE simplifies the process of re-encrypting ciphertexts towards legitimate users via semi-trusted proxies without compromising security or efficiency.
Splitting and Aggregating Signatures in Cryptocurrency Protocols
By: S. Sharmila Deva Selvi, Arinjita Paul, C. Pandu Rangan, Siva Dirisala, Saswata Basu
This work explores the cryptographic efficiency of key splitting and aggregation techniques, which are crucial for improving scalability in blockchain and cryptocurrency protocols. The paper proposes using the BLS short signature scheme, which excels at both key splitting and aggregation, offering enhanced computational efficiency.
About Züs
Zus is an AI-ready decentralized storage solution designed to protect enterprises from Black Swan disasters with unmatched privacy, security, and full on-prem-style ownership and control. Leveraging advanced technologies such as Split Key, Proxy Key, Distributed Data, blockchain-based Unique Identity, and a Zero-Knowledge network, Zus delivers bulletproof data protection for unparalleled peace of mind.
Website: https://zus.network
Enterprise Storage: https://www.blimp.software/
Private Drive: https://www.vult.network/
Contact Information
If you are part of the research team or wish to discuss Züs’s security further, we would love to hear from you at store@zus.network.